Managed IT Services | IT Support Panel
Multi-Factor Authentication (MFA)
Talk to our sales team today to find out how No Doozy IT can provide easy-to-use, secure mobile multi authentication services to your business and employees.
A Modern Fully Managed Multi-Factor (MFA) and Two-Factor (2FA) Solution
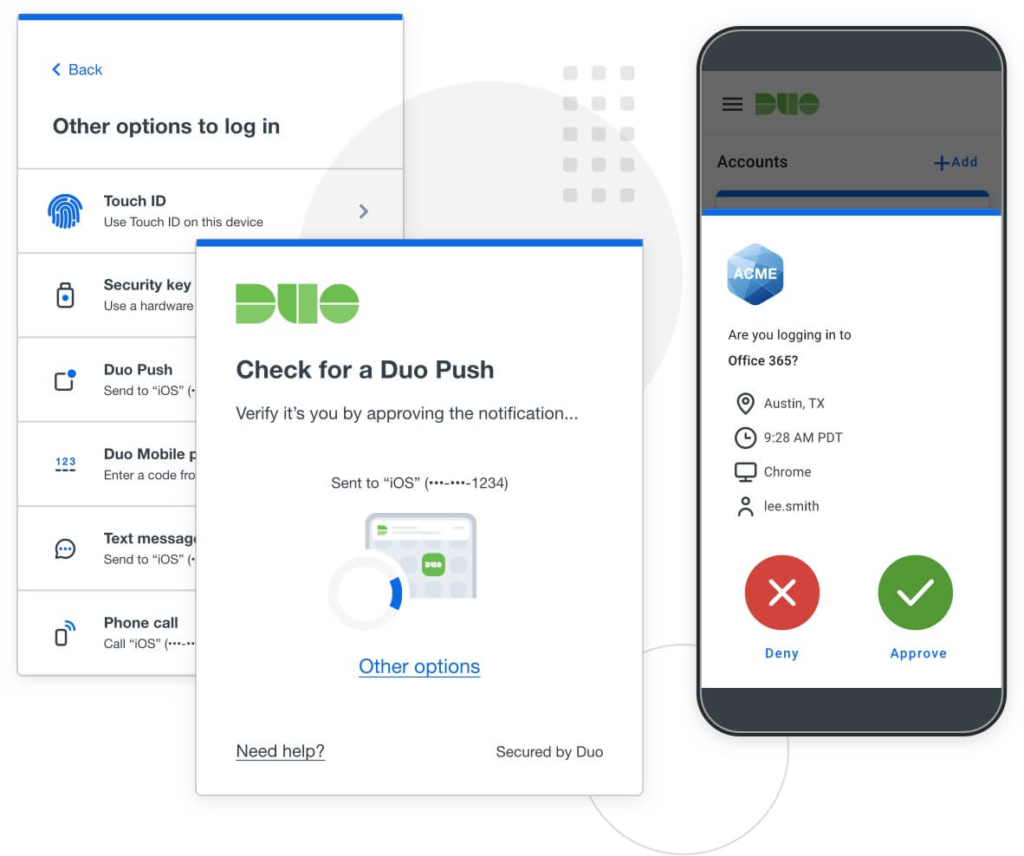
No Doozy IT partnered with Duo to give our clients an MFA that makes multi-factor authentication (MFA) and two-factor (2FA) authentication easy for your employees. With the use of Duo, we can provide an easy-to-use, secure mobile authentication app for quick, push notification-based approval to verify your user’s identity with smartphone, smartwatch and FIDO security key support to all of our managed IT clients. We can also use Duo’s Verified Duo Push option where users are required to input a unique code from the login device into the Duo Mobile app to ensure the identity of the user calling in for IT support.
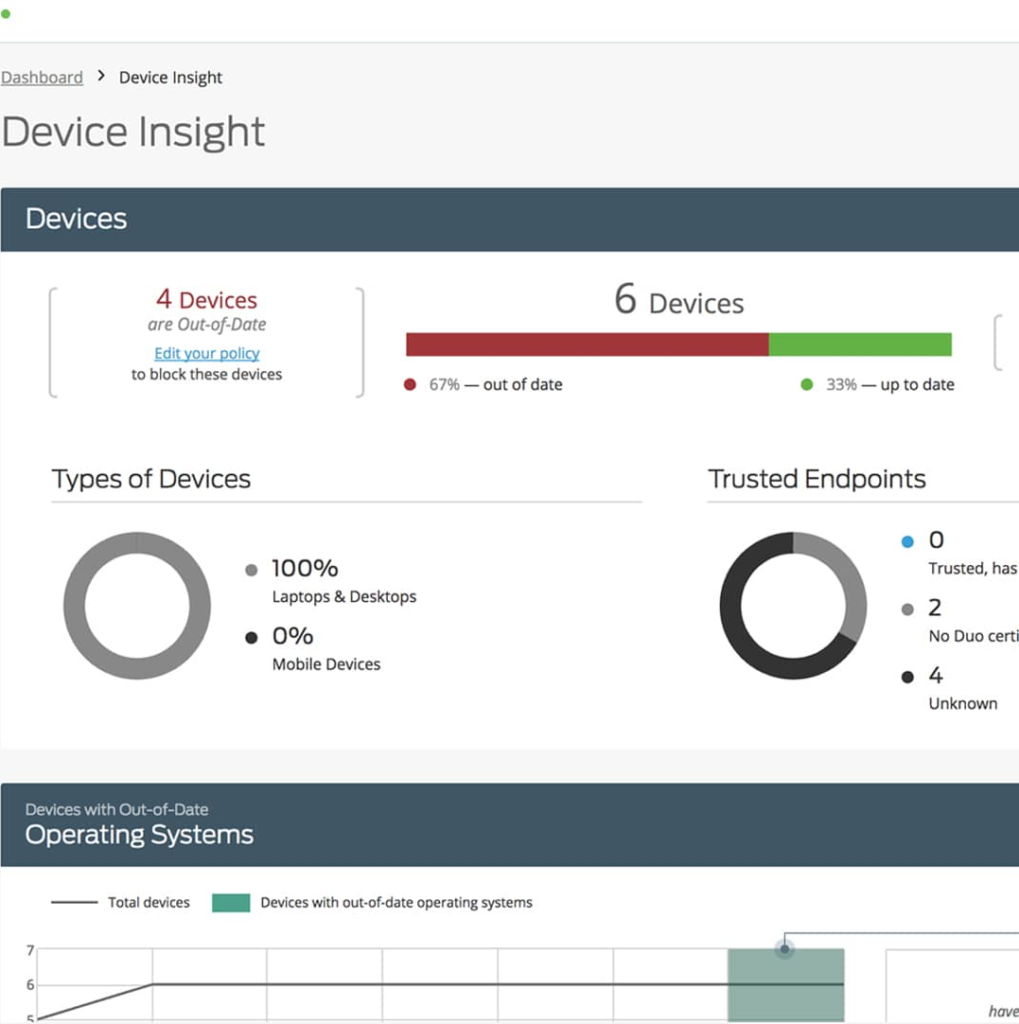
Device Risks At-A-Glance.
No Doozy IT can configure DUO to give your business a high-level summary of the security health of your devices with Duo’s Unified Endpoint Visibility dashboard that populates with data about your devices every time they access your applications.

All No Doozy IT Clients Receive DUO MFA as Part of Their Managed IT Service.
Duo MFA makes multi-factor authentication (MFA) easy for both administrators and users. Duo provides an easy-to-use, secure mobile authentication app for quick, push notification-based approval to verify your user’s identity with smartphone, smartwatch and FIDO security key support. And as No Doozy IT is an authorized Partner of DUO, all of these features are included in ALL of our IT Support plans.

Gain Visibility and Take Control Over BYOD
Bring Your Own Device (BYOD) allows your users to work from anywhere, anytime, increasing productivity. But the problem with allowing personal devices in the workplace is the lack of visibility, control and security for users. With the combination of No Doozy IT and DUO Beyond we can:
- See and Monitor Every Endpoint
- Secure Devices Without an MDM
- Ensure Devices Meet Security Requirements
- Protect On-Premises Applications
- Secure Remote Access to SSH or RDP
- Deny Untrusted Endpoints
The Essential Guide to Device Trust in the Enterprise
Organizations need to enable secure and direct access to business applications for a diverse set of users and devices, but enforcing consistent security policies across managed devices, bringing your own devices (BYOD) and third-party contractor.


Give Us a Call
Still not sure?
Still not sure if you’re a great fit for No Doozy IT?. Let’s have a quick chat about it. Schedule a 15-minute discovery call to find out what value we can deliver to your business.
